Ransomware as a Service ecosystem is gaining popularity among criminals and they are modernizing attack toolkits:
There has been a 51% increase in ransomware incidents reported in H1 2022 compared to the previous year, according to India Ransomware Report H1-2022 released by the Indian Computer Emergency Response Team, or CERT-In.
“Threat actors are continuing to modernize their attack tool kits with high impact strategies. Ransomware as a Service (RaaS) ecosystem is evolving with sophisticated double and triple extortion tactics (Data exfiltration, DDoS) and wide range of ransomware campaigns through affiliates. This is leading to higher probability of monetization and further rise in attack campaigns. Post-covid accelerated digitalization and hybrid work culture are also aiding this threat emergence,” says the report, and adds that threat actors are continuing to exploit known vulnerabilities, compromised credentials of remote access services and phishing campaigns for initial access into the infrastructure of organizations as well as citizens.
UNPATCHED VULNERABILITIES
“Ransomware gangs are focusing on known unpatched vulnerabilities of public-facing applications for initial entry into the network, such as CVE-2019-19781 Vulnerability in Citrix Application Delivery Controller (ADC) and Gateway 10.5, 11.1, 12.0, 12.1, and 13.0 CVE-2021-40539 Vulnerability in Zoho ManageEngine ADSelfService Plus version 6113 and prior. Compromised credentials of remote access services (VPN/ RDP) are being used by threat actors to gain entry into the network and targeted phishing campaigns with embedded payloads like Emotet are also seen for further ransomware infections,” the report explains further.
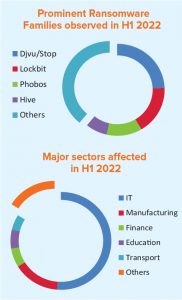
The major sectors affected in H1 2022 are IT, manufacturing, finance, education and transport. “Majority of the attacks are observed in datacentres/IT/ITeS sector followed by manufacturing and finance sectors. Ransomware groups have also targeted critical infrastructure, including oil & gas, transport and power. ‘Drive by download’ is the common tactic in citizen-centric ransomware cases,” says the report.
The report cites the prominent ransomware families in H1 2022 as Djvu/Stop in citizen- centric attacks, Lockbit (2.0 & 3.00) in targeted attacks, Phobos in both citizen-centric and targeted attack campaigns and Hive group in targeted attacks.
It mentions that threat actors are leveraging what is already available in the target environment instead of deploying custom tools and malware. In this way, malicious actions are less likely to flag security controls such as AV/EDR, Windows Binaries, CMD.exe, PowerShell etc.
STEPS IN CASE OF ATTACK
The report suggests steps in case of ransomware attack such as:
– immediately disconnect and isolate infected systems from the network
– disconnect all external storage
– turn off any wireless functionality
– isolate backups immediately
– consider temporarily disabling any external facing remote connectivity service
– report the incident to CERT-In and other regulatory authorities and lodge FIR with law enforcement agencies
– determine the scope of infection for unauthorized access and signs of encryption
– identify mapped or shared drives/folders and network storage devices, external hard drives and USB storage devices, connected networks through MPLS, internet, leased lines, cloud-based storage services, etc.
Efforts should then be made to determine the ransomware strain and check for the ransomware type by evaluating encrypted file extension, ransom note, lock screen, etc.
CERT-In also recommends that the victims should preserve the logs of security devices, end points for necessary analysis, back up the encrypted files, in case a decryptor becomes available, scan the working systems with updated antivirus applications, to determine the malicious binaries, patch any existing vulnerabilities and harden the applications /infrastructure and consider resetting all the account credentials that are possibly compromised and implement Privileged Access Management.
While undertaking restoration of the system, CERT-In recommends that all the infected systems should be rebuilt with fresh installations, making sure to rigorously sanitizing the infected systems/applications/devices before bringing back into the network. The victim should also ensure to follow the best security practices and monitor the network for any suspicious/ anomalous behaviour.
“It is not recommended to negotiate and/or pay the ransom,” says the report.
Read more







